|
assuria product capabilities
more about Assuria Auditor
Assuria AuditorAssuria Auditor provides layers of capability for servers (and critical desktops), the reports provided by Assuria Auditor are designed to assist the user to manage the security and configuration of their servers.
The Vulnerability Detection capability allows Assuria Auditor to detect vulnerabilities on the systems under examination. Vulnerabilities are often associated with poor configuration settings and specific versions of the operating systems, applications and files. Vulnerability data in Assuria Auditor is updated on a regular basis. International standards for vulnerabilities, CVE and CVSS are built into Assuria Auditor. Assuria Auditor provides clear information as to how each vulnerability may be remediated.
The Configuration assurance capability allows Assuria Auditor to examine and compare configuration settings to accepted server security best practice and in accordance with installation requirements. Many security weaknesses are not vulnerabilities but do pose a risk to most installations, for example a server configured with a weak password policy.
The Policy compliance capability Assuria Auditor to report vulnerabilities and configuration setting against the users own standards or external standards such as ISO 27701 or the Payment Card Industry Data Security Standard. With Assuria Auditor reports it is possible to see how your servers match to the different standards.
The Change Detection capability Assuria Auditor to identify and report changes on a system, these changes maybe made to files, registry keys, groups, users, shares, services, software installed. Each detected change should have been previously authorised via a Change Control process and un-authorised changes may indicate malicious activity on your server system. New Change Detection User interface click here.
The System information capability provides information about the server systems, for example the rights and privileges assigned to Groups and Users. Such information is vital to ensure that server security does not degrade over time and that simple controls such as the removal of leavers from user lists is kept up to date.
more about Assuria Log Manager
Assuria Log Manager
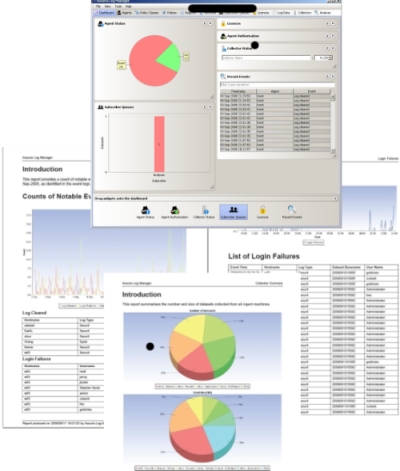
Assuria Log Manager delivers protection and assurance by allowing the user to collect event and audit logs from across the enterprise in secure and forensically sound manner. Data from audit logs can have many uses including monitoring of activities, records of transactions or even used for forensic analysis and evidential use.
Assuria Log Manager provides protection and assurance to installations through layers of capability.
The Event monitoring and alerting capability of ALM provide the ability to configure ALM to monitor for critical events on each server and to generate alerts so that immediate remedial action can be taken.
The Log Collection and secure storage capability is the core to ALM and provides for the secure and forensically sound collection of logs from around the enterprise. ALM is a very scalable solution. Collected logs are stored in their original format in the log store for future forensic or evidential use.
The Log analysis and reporting capability operates once the securely collected and stored logs are in the log store. For compliance reporting the logs are analysed with 'interesting' events being tagged and stored in a SQL database. For unstructured queries and reporting the logs are indexed. Reports are generated from the SQL database or indexed store.
In addition to the powerful out of the box features and facilities Assuria Auditor and Assuria Log Manager allow the user to easily customise to fully satisfy customer’s specific and detailed configuration and security requirements. The level of customisation varies from simple configuration values to in-depth permissions or user permissions and privilege settings.
Automation of Assuria Auditor use is possible using the command line interface. The Command Line Interfaces (CLI) for both the Console and each agent. Using the command line capabilities it is possible to automate most of the routine activities involved in managing your installation with Assuria Auditor and Assuria Log Manager.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
AssuriaOnline
- Download and resources centre